
Solutions for remote sites
Why Ajax
Flexible power supply options
Ajax's portfolio includes 12–24 V⎓ power supply units designed to connect the system to a low-voltage power supply, ensuring the facilities are covered even when no permanent power source is available.
Long-lasting autonomous operation
The hub can operate for over 3 months on a 12 V⎓ gel battery with a 200 A·h capacity. Wireless Ajax devices can operate for up to 7 years on pre-installed batteries.
Maximum communication range
The Ajax hub can communicate with wireless devices at a distance of up to 1,700 m, which can be extended twice with a range extender. It's ideal for covering large areas with multiple buildings or multi-story facilities.
Enhanced security with additional devices
Intrusion sirens and automated devices complete the system, deterring and resisting intruders with a loud sound by activating fog generators or locking automatic gates.
Fortify any facility
Solving any challenge
Intrusion protection
Ajax offers a variety of smart indoor and outdoor devices that operate as a unified force to protect against potential intrusion. The system uses two 4G/LTE communication channels to send alarms to Ajax apps and a central monitoring station (CMS). It can also connect to third-party VHF radio transmitters via Ajax vhfBridge for alarm delivery in areas with unstable internet connections, such as mountains, nature reserves, or desert regions.
Wireless devices for indoor and outdoor security
Wired devices with improved compliance for enhanced security

Connection to the central monitoring station (CMS)

Arming/disarming by specified schedule

Visual verification of alarms
Video surveillance
IP65-rated cameras withstand any weather condition. It’s sabotage-protected and can be reconfigured remotely through Ajax apps. The high-speed video streaming technology delivers exceptional image quality with smooth video archive navigation, and cloud infrastructure provides remote access to the stream from any location.
Secure passwordless camera authentication
Fast and encrypted data transfer

Instant visual verification of alarms in high-resolution
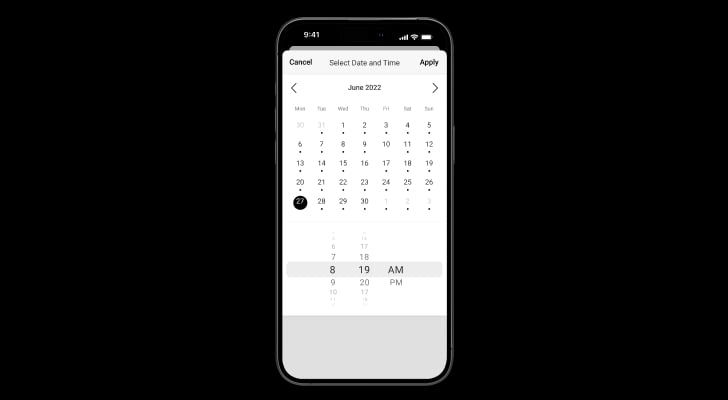
Smooth archive search: calendar view and filters by motion or scenario

NDAA-compliant hardware
Water leak prevention
One Ajax hub can control up to 200 water leak detectors and shutoff valves. Miniature leak detectors suit hard-to-reach places and can be installed without attaching, while the shutoff valve can be integrated into a plumbing system without construction work. In case of an alarm, the system automatically shuts off the water in 7 seconds, quickly preventing any damage.
Compatible with cold and hot water pipes
Up to 3 years of fully autonomous operation with pre-installed batteries

Precise detection and elimination of flooding in a matter of seconds
Automation scenarios to control water supply by schedule or arming mode

Hassle-free integration with an existing plumbing system
Comfort & Productivity
Ajax devices for comfort and productivity create an unparalleled level of control. Air quality monitors provide temperature and humidity readings with medical-grade accuracy to maintain the required microclimate inside the premises. Smart relays, sockets, and switches seamlessly manage various appliances, ventilation, lighting, roller shutters, and gates with remote in-app control and programmable scenarios.
It takes a few minutes to configure automation scenarios in Ajax apps
The system activates scenarios even when there is no Internet connection

Simulating the owner's presence on the site

De-energizing the facility in response to fire alarm

Temperature and humidity monitoring at the buildings under renovation

Build your own security
Use a configurator to create a custom kit of Ajax devices that will cover your request
Customer stories
Discover how the world becomes a safer place with Ajax
More Ajax superpowers
Explore further the essential benefits of Ajax that have been useful for users at remote facilities

Informative notifications and detailed event log
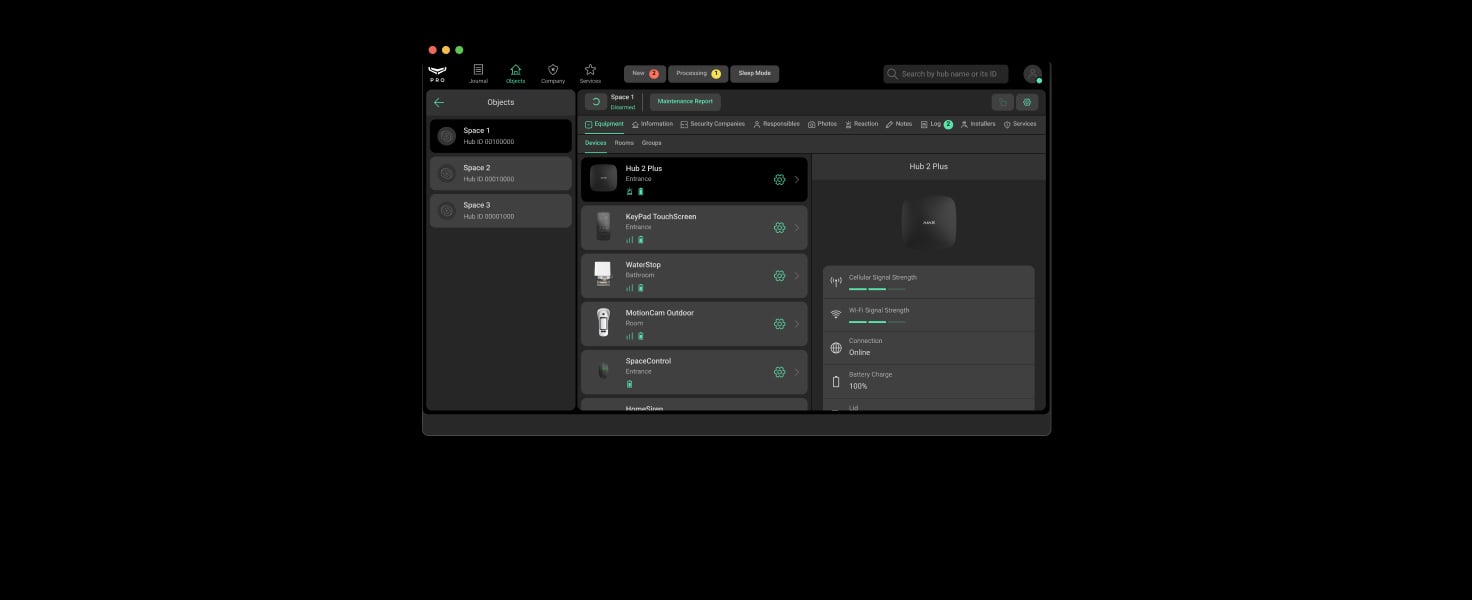
Monitoring with PRO Desktop app
Countermeasures to deal with intruders

Effortless to install and relocate

Implement a similar project
Authorized Ajax partners are ready to develop a customized security solution for your facility. Leave your contact details to request a quote.
FAQ
What security measures are essential for protecting remote properties
For remote properties, focus on sturdy fencing and advanced security systems equipped with motion detectors, cameras, and remote monitoring to deter theft and vandalism. These measures are vital due to the vulnerability of remote properties.
What is a remote security system
A remote security system is a set of connected devices and technologies designed to monitor and protect properties or assets from a distance. It typically includes cameras, motion detectors, sirens, and access control devices. These systems can be accessed and managed remotely via mobile apps, allowing users to monitor their property's security status in real time and receive alerts in case of suspicious activity. Remote security systems provide peace of mind by offering continuous surveillance and control over the protected area, even when the user is off-site.
How can homeowners ensure the effectiveness of security systems in remote properties
Homeowners can ensure the effectiveness of security systems in remote properties by prioritizing features that promptly alert administrators and monitoring stations of intrusions. In remote areas, where help may be far away, intruders have time to act. Therefore, loud sirens and automated responses are crucial for swift deterrence. Video surveillance plays an important role here, as it captures intruders and helps in further actions.
What security challenges do remote properties face
Remote properties face unique challenges due to their distance from populated areas and the lack of constant supervision. They are vulnerable to physical threats such as theft and vandalism, with limited access to immediate assistance. This underscores the importance of implementing comprehensive security measures tailored to the remote environment.

















