MotionCam (PhOD) Fibra
Soon to be: Superior MotionCam (PhOD) Fibra
Wired IR motion detector that takes on-demand photos and photos by alarm, schedule, and scenario
Product is not available in your region

The product name will change soon
It is one of many updates to the Ajax portfolio segmentation.
New standard on intrusion detection
MotionCam (PhOD) has a built-in camera that takes photos once the detector is triggered. It needs just 9 seconds to show the actual situation on the scene. With visual evidence available in Ajax apps, the security company can quickly check whether the threat is real to respond accordingly. Photo verification relieves users of unnecessary anxiety and security companies of false patrol calls. It takes a click for the user to take an on-demand photo at any time to monitor the house's state. Also, the detector can automatically take pictures by an alarm of another device in the system and by a specific schedule.
Key features
In an Ajax system, you can combine devices of all product categories: Intrusion protection (both Superior and Baseline), Video surveillance, Fire and life safety, or Comfort and automation. Create the system to suit your needs and manage it in a single interface.
This is the device of the Superior product line. Only accredited Ajax Systems partners can sell, install, and administer Superior products.
Wherever there is a risk of intrusion
Peace of mind on demand
MotionCam (PhOD) needs just a few seconds to show the actual situation on the scene and dispel the user's doubts in case of an alarm. It takes a click in the Ajax app to take an on-demand photo. Also, it can automatically take pictures at specific times or when selected devices in the system activate an alarm.




Privacy first
MotionCam (PhOD) is designed to control security, not privacy. Photos are protected from prying eyes at the detector, system, and software levels.




Also, the Ajax product portfolio includes the MotionCam Fibra detectors without Photo on Demand, Photo by Scenario, and Photo by Schedule functions.
Discover future-proof hardware

Fresnel lens

PIR sensor

Camera

IR backlight in low light conditions

Backup battery

SmartBracket mounting panel with removable terminal board
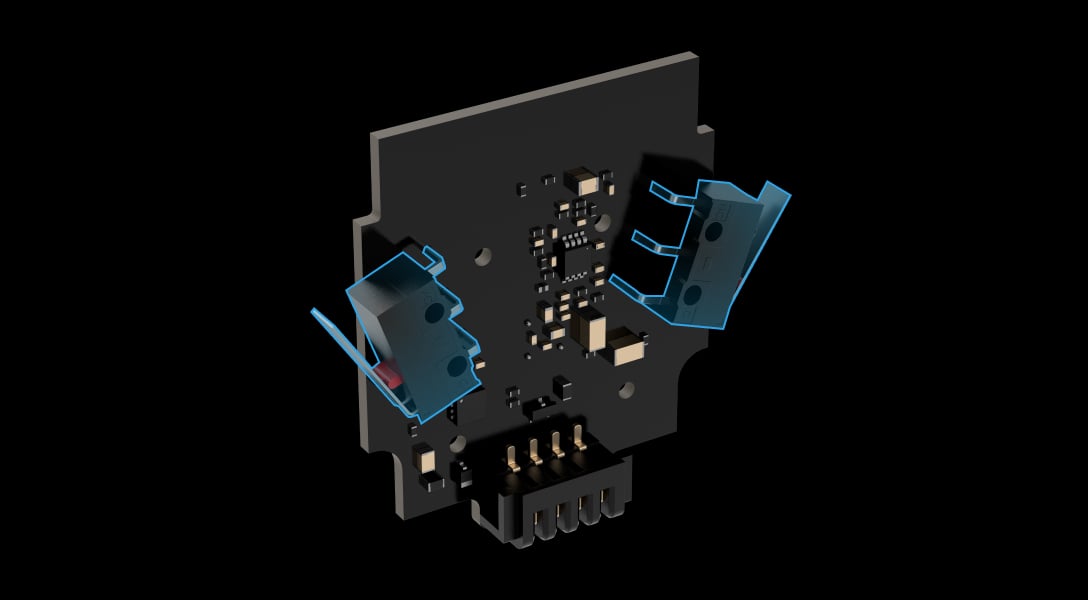
Two tampers

Holding screw to secure the detector on SmartBracket
No intruder goes unnoticed
PIR sensor
All Ajax motion detectors use PIR sensors by Excelitas Technologies — a field-leading American manufacturer specializing in designing and producing optronic components since 1931. Ajax Systems constantly proves the sensor's superior quality at the production stage: we test 100% of manufactured devices. Wrapped into Ajax technologies, it brings the utmost accuracy of intrusion detection.

Special lens
The pattern of the Fresnel lens sections is designed to differentiate between the IR diagrams of a human, animal, and thermal noise. Large lens sections capture radiation at an adult's head and torso level. Smaller sections make the diagram more detailed. The lens provides the detector with accurate information about the thermal object in the detection zone and the nature of its movement.

Thermal interferences filter

We processed thousands of thermal patterns caused by humans, animals, and the environment to develop the SmartDetect software algorithm. In armed mode, the detector constantly analyses the thermal diagram from the PIR sensor, including the IR radiation intensity, thermal spot size, movement speed, time spent in the detection zone, and other parameters. The algorithm identifies false alarm markers instantly and with high accuracy. As a result — the detector accurately responds to human motion without false alarms.
False alarm
Real alarm

False alarm
Real alarm
False alarm
Real alarm
Temperature compensation
Temperature compensation is a software mechanism keeping the thermal diagram contrast even if the ambient temperature is close to the temperature of the human body. With each ambient temperature measurement, the detector corrects the PIR sensor data according to the coefficient table stored in its memory. The detector is effective over the entire operating temperature range.

Sensitivity level
The detector can adapt to the conditions of a particular facility, considering possible thermal interference or pets. The sensitivity setting changes the set of markers by which false alarms are filtered. Low sensitivity makes the detector less likely to respond to an active pet. A high sensitivity will raise the alarm in case of any motion in the detection zone.
Professional installation
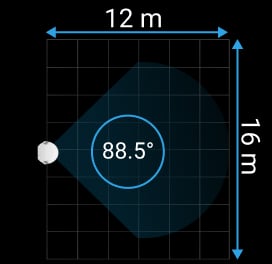
With the correct installation at the height of 7.87 ft and lens direction perpendicular to an alleged intrusion path, the detector provides an accurate thermal diagram and pet immunity. It instantly responds to a real threat, minimising false alarms caused by animals weighing up to 44 lb and below 1.64 ft in height.

Fibra
Unique wired technologies
The Ajax system uses secure two-way communication based on Fibra proprietary protocol. It features encryption and device authentication to prevent sabotage, spoofing, or data theft. Fibra lines are multifunctional and support connecting different types of devices to one line: sirens, keypads, and detectors with photo verification.

Up to 6,562 ft of communication range with an Ajax hub3 or a module that extends the Fibra line
One line for different types of devices
Photo delivery by Fibra line without interference
Protection against sabotage and spoofing
Energy efficiency as a priority
Fibra communication requires minimum power consumption. Also, MotionCam (PhOD) is hardwired with a backup battery to power the sensor, LED indicator, and camera during alarms. The battery has an optimized charging algorithm which uses the minimum energy required to fully recharge without affecting other connected devices.
Built-in backup battery
Optimized charging algorithm
Power consumption of up to 0.12 W

System supervision
All Ajax devices perform automatic self-diagnosis and report their states to the hub. Essential parameters, including tamper, communication, power supply, and sensor statuses, are continuously monitored. The Ajax Cloud server controls communication between the hub and Ajax apps, ensuring instant notifications for ARCs, security companies, and users. In case of any malfunction or communication failure, an engineer is informed immediately to provide necessary services.
Automatic device self-diagnosis with status report
Regular polling to display the current device state on apps
Instant maintenance notifications

Sabotage-resistant






Next-level protection of Fibra line
Introducing LineProtect, the module designed to protect an Ajax hub and connected wired devices from sabotage when intruders cause overvoltage and short circuits, apply 110/230 V~, or use stun guns.
PRO is king
The myth about wired systems being difficult to install is busted. Ajax minimized an expensive, long, and dusty experience for PROs by developing an ultimate set of tools to make the process easy and flexible, from project design to client support and system maintenance. There is no need to disassemble the device for installation. Intuitive Ajax apps help quickly make the device a part of the system, and each device can always be reconfigured remotely without site visits. No need for programmers — everything is available out-of-box.
Fibra power supply calculator
The online tool provides security specialists with comprehensive information about the devices’ power consumption. It's easy to check before installation whether the wired system project will work in practice. The calculator allows real-time project-making, highlighting the problem areas and offering solutions. Once the calculations are finished, the results can be downloaded as a PDF file.
With the SmartBracket panel, an installer can effortlessly mount the device on the wall. The installation kit includes all the necessary fasteners. There is no need to disassemble the device: the board with terminals is placed outside the enclosure under SmartBracket to eliminate hardware damage during installation. The board is removable, which makes the whole process more comfortable. For cable management, there are bracings inside SmartBracket to secure the wires with ties. The detector can be installed sideways: the enclosure has two tampers on the left and right sides.
No need to disassemble the detector’s enclosure
Can be installed sideways
Removable terminal board
All the necessary fasteners included in the installation kit
Holding screw to secure the detector on a mounting panel

The device is paired with the hub automatically via Fibra line scanning. This tool is available in the desktop or mobile PRO apps. An installer only needs to name the device and assign it to the room and security group. The device can also be added by scanning the QR code or entering its ID manually.
Pairing with a hub via automatic line scanning or QR code
Device identification by triggering or LED indication
Optimal default settings to cover major requests

Intuitive Ajax apps provide remote set-up and all detector information from anywhere the Internet is available, on a smartphone or PC. An installer can remotely change the settings and provide services in-time. No need to visit the object.
Remote configuration without site visits
Apps for iOS, Android, macOS, and Windows
Accounts for companies and installers

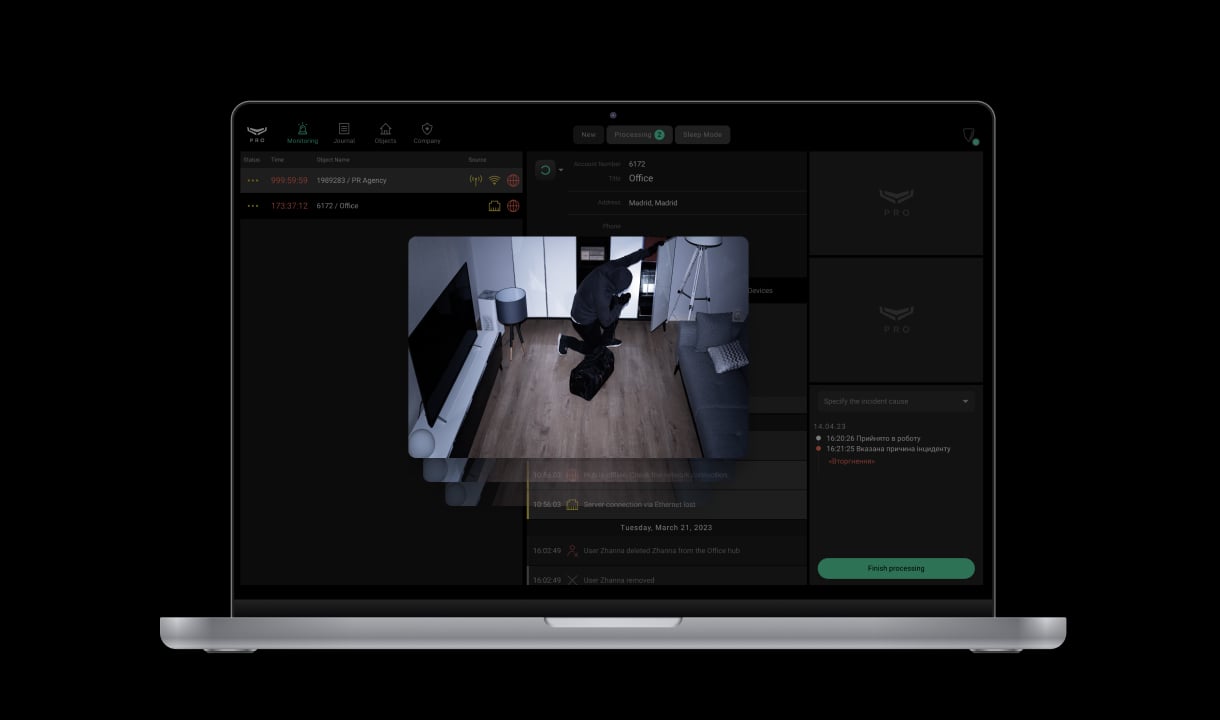
MotionCam (PhOD) Fibra has two-way communication and ultimate informativeness. The security company will receive an alarm notification in less than a second. Notifications include all the necessary information: name of the device, time of the event, and even the exact room where the device is located. CMS also receives photo verification, capturing the reason for the alarm.
Full addressability of connected devices
Instant notifications in Ajax apps
Alarms and events monitoring in PRO Desktop for security companies
Out-of-the-box photo verification support
With default settings (photo resolution is 320×240 px).
According to INCERT certification, detection range is up to 32.8 ft.
With U/UTP cat.5, 4 × 2 × 0.51 cable. Other cable types may have different values. Please use Fibra power supply calculator to check the wired system project before installation.
Technical information
More MotionCam models
Ajax product categories
In an Ajax system, you can combine devices of all product categories: Intrusion protection (both Superior and Baseline), Video surveillance, Fire and life safety, or Comfort and automation. Create the system to suit your needs and manage it in a single interface.