MotionCam (PhOD) Jeweller
Wireless IR motion detector supporting photo by alarm, photo on demand, photo by schedule, and photo by scenario features
Lightning-fast alarms. Verified.
MotionCam (PhOD) Jeweller has a built-in camera that takes photos once the detector is triggered. It needs just 9 seconds to show the actual situation on the scene. With visual evidence available in Ajax apps, the security company can quickly verify the threat and respond accordingly. Photo verification relieves users of unnecessary anxiety and prevents security companies from false patrol calls. Users can take an on-demand photo with a single tap to monitor their house's state at any time. The detector can also automatically take photos by an alarm of another device in the system and by a specific schedule.
Discover PhOD detectors
Introducing motion detectors supporting photo by alarm, photo on demand, photo by schedule, and photo by scenario features
Watch on YoutubeKey features
In an Ajax system, you can combine devices of all product categories: Intrusion protection (both Superior and Baseline), Video surveillance, Fire and life safety, or Comfort and automation. Create the system to suit your needs and manage it in a single interface.
Awards

Wherever there is a risk of intrusion
Peace of mind on demand
The detector needs just a few seconds to show the actual situation on the scene and dispel the user's doubts in case of an alarm. It takes a click in the Ajax app to take an on-demand photo. Also, it can automatically take photos by schedule and when another detector in the system is triggered.




Privacy first




The Ajax product portfolio includes motion detectors without Photo on Demand, Photo by Schedule, and Photo by Scenario functions. These detectors support visual alarm verification and do not feature PhOD in their names.
Discover future-proof hardware

Fresnel lens

PIR sensor

Camera

IR backlight for low-light conditions

Pre-installed batteries

Tamper

Jeweller and Wings antennas

SmartBracket mounting panel
No intruder goes unnoticed
PIR sensor
All Ajax motion detectors use PIR sensors by Excelitas Technologies — a field-leading American manufacturer specializing in designing and producing optronic components since 1931. Ajax Systems constantly proves the sensor's superior quality at the production stage: we test 100% of manufactured devices. Wrapped into Ajax technologies, it brings the utmost accuracy of intrusion detection.

Special lens
The pattern of the Fresnel lens sections is designed to differentiate between the IR diagrams of a human, animal, and thermal noise. Large lens sections capture radiation at an adult's head and torso level. Smaller sections make the diagram more detailed. The lens provides the detector with accurate information about the thermal object in the detection zone and the nature of its movement.

Thermal interferences filter

We processed thousands of thermal patterns caused by humans, animals, and the environment to develop the SmartDetect software algorithm. In armed mode, the detector constantly analyzes the thermal diagram from the PIR sensor, including the IR radiation intensity, thermal spot size, movement speed, time spent in the detection zone, and other parameters. The algorithm identifies false alarm markers instantly and with high accuracy. As a result — the detector accurately responds to human motion without false alarms.
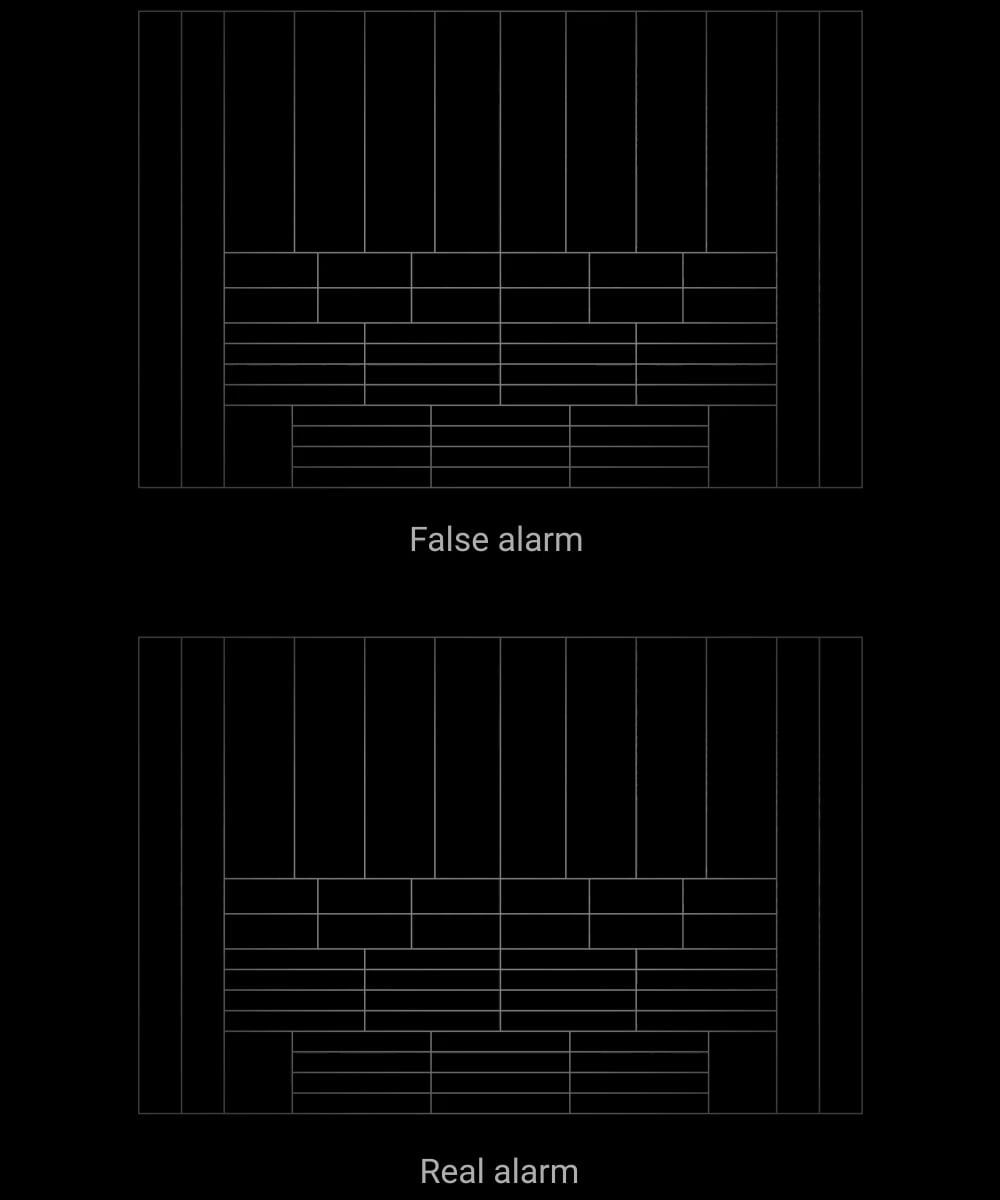
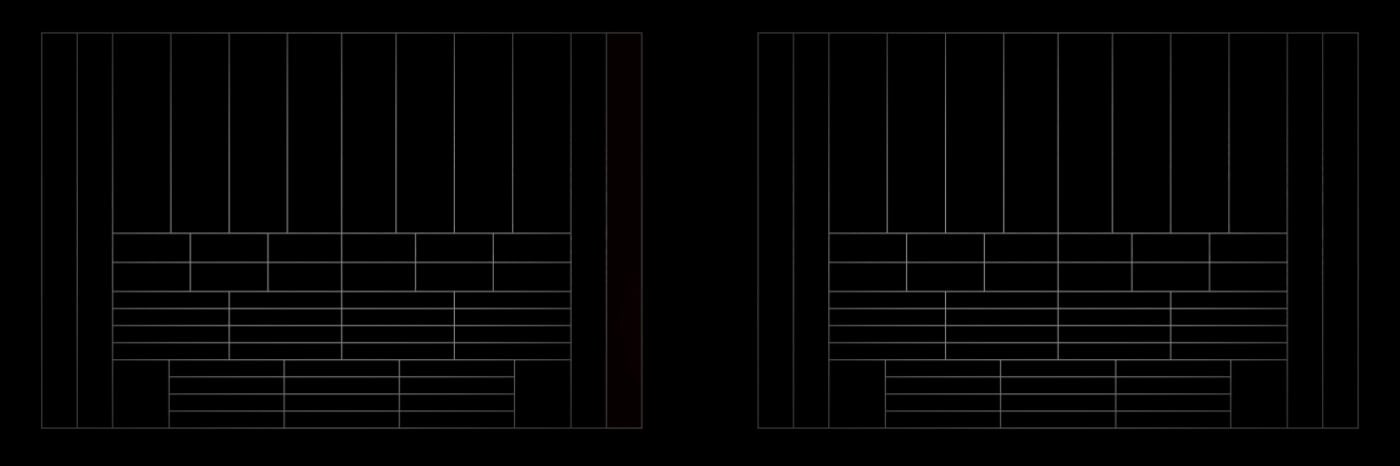
False alarm
Real alarm

False alarm
Real alarm
False alarm
Real alarm
Temperature compensation
Temperature compensation is a software mechanism keeping the thermal diagram contrast even if the ambient temperature is close to the temperature of the human body. With each ambient temperature measurement, the detector corrects the PIR sensor data according to the coefficient table stored in its memory. The detector is effective over the entire operating temperature range.

Sensitivity level
The detector can adapt to the conditions of a particular facility, considering possible thermal interference or pets. The sensitivity setting changes the set of markers by which false alarms are filtered. Low sensitivity makes the detector less likely to respond to an active pet. A high sensitivity will raise the alarm in case of any motion in the detection zone.
Professional installation
With the correct installation at the height of 2.4 m and lens direction perpendicular to an alleged intrusion path, the detector provides an accurate thermal diagram and pet immunity. It instantly responds to a real threat, minimizing false alarms caused by animals weighing up to 20 kg and below 50 cm in height.

Stable operation with pre-installed batteries
MotionCam (PhOD) Jeweller comes equipped with pre-installed batteries, boasting a remarkable 5-year lifespan. Ajax apps proactively notify both the monitoring company and users of a low battery level a couple of months in advance. The batteries are replaceable, allowing the installer to simply swap them out after five years. Thanks to the batteries, MotionCam (PhOD) Jeweller functions independently of the facility’s power grid.
Up to 5 years of operation from pre-installed batteries
Low battery level warning
Replaceable CR123A batteries


Jeweller | Wings
Unique wireless technologies
MotionCam (PhOD) uses Jeweller and Wings proprietary radio protocols for reliable communication
Up to 1,700 m of radio communication3 with a hub or range extender
Encrypted two-way radio communication
Notifications about jamming and connection loss
9 seconds1 to deliver the first photo
Scaled and comprehensive
ReX 2 Jeweller range extender boosts the range of all Ajax devices and manages their communication with the hub via Jeweller. It also assures stable communication through steel and concrete via Ethernet using the wire as the additional communication channel. Up to 5 range extenders can operate within one Ajax system to expand the network twice as big, covering multistorey buildings with underground parking and basements.
Up to 5 range extenders within one system
Ethernet as an alternative communication channel



System supervision
All Ajax devices perform automatic self-diagnosis and report their states to the hub. Essential parameters, including tamper, communication, power supply, and sensor statuses, are continuously monitored. The Ajax Cloud server controls communication between the hub and Ajax apps, ensuring instant notifications for ARCs, security companies, and users. In case of any malfunction or communication failure, an engineer is informed immediately to provide necessary services.
Automatic device self-diagnosis with status report
Regular polling to display the current device state on apps
Instant maintenance notifications

Sabotage-resistant





Effortless installation and setup
MotionCam (PhOD) is ready to operate straight out of the box. Using the SmartBracket panel, an installer can effortlessly mount the device on the wall, eliminating the need to disassemble the enclosure. Ajax apps help quickly make the device a part of the ecosystem: simply pair the device with the hub by scanning the QR code. It can always be reconfigured remotely without the need for on-site visits.
Pairing with the hub via QR code
SmartBracket panel — no need to disassemble the enclosure

Configuring and testing in mobile and desktop apps

PRO Desktop app for macOS and Windows

- 1 With default settings (photo resolution is 320 × 240 px).
- 2 The HDR image feature is available for devices with the 15.59.35.14 firmware version or later. Сontact your Ajax Systems manager, supplier, or authorized partner to check the availability in your region.
- 3 In an open space.
Technical information
MotionCam (PhOD) Jeweller
More MotionCam models
Ajax product categories
In an Ajax system, you can combine devices of all product categories: Intrusion protection (both Superior and Baseline), Video surveillance, Fire and life safety, or Comfort and automation. Create the system to suit your needs and manage it in a single interface.
Wireless motion detectors with photo verification in the security system
Motion sensors of the security system are designed to record the fact of unauthorized entry into the property under security. When the motion sensor is activated, its signal is transmitted to the alarm central via a wire or radio signal, depending on the type of system.How motion sensors work
Motion sensors analyze microwave, ultrasonic, infrared and radio type radiation. If movement was noticed in the room, the sensor detects changes in the parameters of incoming waves and activates a certain reaction to the event. When triggered, the motion sensor sends data to the alarm control panel, informs the user, and initiates the activation of the siren.Types of motion sensors
Motion sensors differ in:- The type of reaction to alarm: these are ultrasonic devices, infrared, microwave and combined type.
- Place of installation: outdoor and indoor devices.
- Data transmission method — wireless or wired system.
- Wave processing and creation mechanism — active and passive models that process radiation at the input.
How to choose a motion sensor for a security system
In order to choose a motion sensor for alarming correctly, it is worth considering the features of the devices:- First you need to choose the type of installation of the motion sensor — on the wall or ceiling. With the choice of location, the installation engineer will best help.
- The presence of immunity to animals, which helps to avoid false alarms on pets.
- Energy consumption level — the amount of electricity that the sensor consumes.
- The angle and radius of detection — this determines how large a territory the motion sensor can control.
- Customizable — adjusting the weight and height of the object to which you want to respond.
- The speed of the motion sensor's response to an alarm.
- Case protected from opening and damage.